What is Risk Assessment?
Risk assessment is a systematic process that involves identifying, analyzing, and evaluating potential risks or uncertainties that can affect the achievement of objectives, projects, or activities. It’s a crucial tool for understanding and managing uncertainties in various contexts, from business operations and project management to healthcare and environmental planning.
Why is Risk Assessment Important?
- Informed Decision-Making: Risk assessment provides critical information that allows individuals and organizations to make informed decisions by weighing potential risks and rewards.
- Preventive Measures: It helps in identifying and addressing potential issues before they escalate into costly problems, thereby saving resources and minimizing negative impacts.
- Resource Allocation: By prioritizing risks, organizations can allocate their resources more efficiently, focusing on high-impact risks that require immediate attention.
- Compliance: In many industries, risk assessments are essential for compliance with regulatory requirements and standards.
- Continuous Improvement: Risk assessment is an ongoing process that fosters a culture of continuous improvement by learning from past experiences and adapting to changing circumstances.
Why Conduct Risk Assessment?
The primary purpose of risk assessment is to systematically evaluate uncertainties and potential threats, allowing for effective risk management. Here’s a closer look at its core objectives:
- Identify Risks: The first step is to identify and recognize potential risks that could impact your objectives, projects, or operations. This step involves gathering data, conducting assessments, and consulting stakeholders to ensure a comprehensive view of risks.
- Analyze and Prioritize: Once identified, risks are analyzed to understand their nature, causes, and potential consequences. Prioritization helps focus resources and efforts on managing the most critical risks.
- Mitigate or Manage: After prioritization, risk mitigation or management strategies are developed and implemented to reduce the likelihood or impact of identified risks. These strategies can include risk avoidance, risk reduction, risk transfer, risk acceptance, and contingency planning.
- Monitor and Review: Risk assessment is an ongoing process that requires constant monitoring and periodic reviews. This ensures that risks are continually evaluated, and mitigation strategies are adjusted as needed.
- Improve Decision-Making: Risk assessment provides decision-makers with valuable insights to make informed choices, allocate resources effectively, and proactively address potential challenges.
Benefits of Effective Risk Assessment
Effective risk assessment offers numerous advantages to individuals and organizations across various domains:
- Enhanced Preparedness: By identifying and analyzing potential risks, organizations become better prepared to respond to adverse events, reducing the likelihood of crises.
- Improved Resource Allocation: Prioritizing risks ensures that resources are allocated to address high-impact risks, maximizing the return on investment in risk management.
- Regulatory Compliance: Many industries require risk assessments to meet regulatory compliance. Effective risk assessment helps organizations adhere to legal and industry standards.
- Business Continuity: Effective risk management safeguards business continuity by identifying vulnerabilities and implementing measures to mitigate potential disruptions.
- Stakeholder Confidence: Demonstrating a proactive approach to risk management fosters stakeholder trust and confidence, which is crucial for business relationships and reputation.
- Cost Savings: By identifying and addressing risks early, organizations can avoid costly crises, litigation, and operational interruptions.
- Strategic Advantage: Effective risk assessment allows organizations to identify and seize opportunities that may otherwise go unnoticed or unexplored.
In summary, risk assessment is a fundamental process for understanding, managing, and ultimately thriving in a world filled with uncertainties. Its importance spans across industries and domains, offering a structured approach to proactive decision-making and risk management.
Key Elements of Risk Assessment
Risk assessment involves several key elements that work together to ensure a comprehensive evaluation of potential risks. Let’s explore each element in more detail:
Identification of Risks
Risk identification is the foundational step in the risk assessment process. To identify risks effectively, you should:
- Diversify Your Sources: Encourage input from a wide range of stakeholders, including team members, subject matter experts, and relevant parties outside your organization.
- Utilize Risk Categories: Classify risks into categories such as financial, operational, strategic, and compliance-related to ensure a systematic approach.
- Learn from Historical Data: Analyze past projects, incidents, or similar endeavors to identify recurring risks and patterns.
- Implement Risk Register: Maintain a dynamic risk register that records all identified risks, their descriptions, potential consequences, and current status.
Risk Analysis
Risk analysis is where you delve deeper into the nature of identified risks. Consider these aspects when conducting risk analysis:
- Quantitative vs. Qualitative Analysis: Decide whether to use quantitative methods involving numerical values or qualitative approaches based on expert judgment, depending on the nature of the risk.
- Probability Assessment: Assess the likelihood of each risk occurring. Utilize historical data, expert opinions, and analytical tools to make informed judgments.
- Impact Assessment: Evaluate the potential impact of each risk on your project, organization, or objectives. Consider both the immediate and long-term consequences.
- Risk Assessment Models: Familiarize yourself with various models, such as decision trees, sensitivity analysis, and risk matrices, to quantify risks effectively.
- Data Gathering Techniques: Employ data collection techniques like surveys, interviews, and document analysis to gather relevant information for analysis.
Risk Evaluation
Risk evaluation involves determining the significance of each identified risk and making informed decisions about how to address them:
- Risk Severity Assessment: Develop a clear understanding of the potential severity of each risk. Consider the extent to which it can disrupt your goals and objectives.
- Risk Prioritization: Prioritize risks based on their severity, likelihood, and potential impact. This step helps you focus resources on the most critical risks.
- Risk Tolerance and Acceptance: Define your organization’s risk tolerance level. Decide which risks are within acceptable limits and which require mitigation efforts.
- Stakeholder Engagement: Involve key stakeholders in the risk evaluation process to ensure a holistic perspective and align risk management strategies with organizational goals and values.
Risk Mitigation Strategies
Once you’ve identified, analyzed, and evaluated risks, it’s time to implement strategies to mitigate or manage them effectively:
- Risk Avoidance: In some cases, the best strategy is to avoid the risk altogether. This may involve altering project plans, processes, or strategies to eliminate high-impact risks.
- Risk Reduction: Implement measures to reduce the likelihood or impact of identified risks. This might include redundancy planning, process improvement, or enhanced security measures.
- Risk Transfer: Consider transferring certain risks to third parties. For example, you can purchase insurance to transfer financial risks or outsource specific activities to mitigate operational risks.
- Risk Acceptance: Acknowledge that some risks are within acceptable limits and do not require active mitigation. However, be prepared with contingency plans to respond if these risks materialize.
- Contingency Planning: Develop well-defined contingency plans for high-impact risks that cannot be entirely avoided, reduced, or transferred. These plans should outline specific actions to take in case the risk manifests.
How to Prepare for Risk Assessment?
Effective preparation is key to conducting a successful risk assessment. To ensure a smooth process, consider the following steps:
Establishing a Risk Assessment Team
The composition of your risk assessment team is crucial. Assemble individuals with diverse expertise and perspectives, including:
- Subject Matter Experts: Those with in-depth knowledge of the industry, project, or specific risks.
- Decision-makers: Individuals responsible for making final decisions based on risk assessment findings.
- Team Members: Those directly involved in the project or decision-making process.
A well-rounded team ensures that all potential risks are considered and evaluated thoroughly.
Defining Scope and Objectives
Clearly defining the scope and objectives of your risk assessment is essential to its success. Consider these aspects:
- Project Scope: Determine the boundaries of the risk assessment, specifying what is included and excluded from the evaluation.
- Objectives: Establish clear and measurable objectives for the risk assessment, defining what you aim to achieve through the process.
- Key Deliverables: Identify the expected outputs, such as a risk register, risk assessment reports, and mitigation plans.
Defining these parameters provides a roadmap for your risk assessment, keeping it focused and aligned with your goals.
Gathering Relevant Data and Information
Accurate and up-to-date data is the lifeblood of effective risk assessment. Ensure you:
- Identify Data Sources: Determine where the necessary data and information can be sourced. This may include internal documents, external reports, industry benchmarks, and expert opinions.
- Data Quality Assurance: Verify the accuracy and reliability of the data you collect. Inaccurate or outdated data can lead to flawed risk assessments.
- Data Storage and Organization: Implement systems or tools for storing and organizing data, ensuring easy access when needed during the assessment process.
- Data Security and Privacy: Consider data security and privacy regulations to protect sensitive information.
Legal and Ethical Considerations
Before proceeding with your risk assessment, be aware of the legal and ethical considerations that may impact your process:
- Legal Compliance: Ensure that your risk assessment activities comply with applicable laws and regulations. This is especially important in industries with strict compliance requirements.
- Ethical Standards: Uphold ethical standards throughout the assessment process. This includes respecting privacy, maintaining confidentiality, and avoiding conflicts of interest.
- Informed Consent: When collecting data from individuals or stakeholders, obtain their informed consent, and ensure they understand the purpose and implications of the assessment.
- Transparency: Communicate openly about the risk assessment process, its objectives, and how the findings will be used.
Addressing legal and ethical considerations not only safeguards your organization but also builds trust with stakeholders involved in the assessment.
Risk Identification
Risk identification is a critical phase of risk assessment, where you systematically identify potential risks that may affect your project, organization, or objectives. Let’s dive deeper into the key components of risk identification:
Types of Risks
Understanding the various types of risks is essential to comprehensively identify potential threats and opportunities. Common types of risks include:
- Financial Risks: These encompass economic factors, market fluctuations, currency exchange rates, and financial instability.
- Operational Risks: Operational challenges may involve process inefficiencies, supply chain disruptions, or technology failures.
- Strategic Risks: Risks associated with strategic decisions, including market competition, changing customer preferences, or shifts in industry trends.
- Compliance Risks: These involve legal and regulatory issues, non-compliance with industry standards, or violations of environmental and social responsibilities.
- Reputation Risks: Risks that can harm your organization’s image, such as public relations crises or ethical lapses.
- Project Risks: Risks specific to project management, such as scope changes, resource constraints, or delays.
- Safety Risks: Risks related to the health and safety of employees, customers, or the public.
Identifying the relevant risk types helps you focus your assessment efforts and tailor mitigation strategies accordingly.
Internal and External Risk Factors
Risks can originate from both internal and external factors. Distinguishing between these sources is crucial for a holistic risk identification process:
- Internal Risk Factors: These originate within your organization and are often under your control. Examples include operational inefficiencies, employee turnover, or inadequate resource allocation.
- External Risk Factors: External risks are beyond your organization’s direct control and often result from external forces, such as economic downturns, natural disasters, political instability, or changes in market dynamics.
By recognizing the source of a risk, you can better determine how to address it, whether through internal process improvements or external contingency planning.
Risk Sources and Causes
Identifying the sources and underlying causes of risks is essential for targeted risk mitigation:
- Source of Risk: This refers to the origin or starting point of a risk. Sources can include specific processes, activities, technologies, or external events.
- Risk Causes: Understanding the root causes of risks is crucial for effective risk management. Causes can be multifaceted and may include human error, system vulnerabilities, market fluctuations, or regulatory changes.
By identifying both the source and causes of a risk, you can develop strategies to prevent or mitigate these factors.
Risk Register and Documentation
A well-maintained risk register is a vital tool in risk identification. It serves as a central repository for recording and tracking identified risks. Key elements of a risk register include:
- Risk Description: A detailed description of the risk, including its nature, potential consequences, and any related factors.
- Risk Probability: An estimate of the likelihood of the risk occurring, often expressed as a percentage.
- Risk Impact: An assessment of the potential consequences or severity of the risk on your project, organization, or objectives.
- Risk Owner: Designate a responsible individual or team accountable for managing and monitoring each risk.
- Risk Status: Indicate the current status of the risk, whether it’s actively monitored, in mitigation, or resolved.
- Mitigation Strategies: Document specific actions and plans for mitigating or managing each risk.
A well-documented risk register ensures that all identified risks are systematically addressed and monitored throughout the risk assessment process.
Risk Analysis
Risk analysis involves a deeper examination of identified risks to quantify their potential impact and likelihood. Here’s a closer look at the key aspects of risk analysis:
Quantitative vs. Qualitative Analysis
Risk analysis can be approached using either quantitative or qualitative methods, depending on the nature of the risk and the availability of data:
- Quantitative Analysis: Involves assigning numerical values to risks, such as assigning probabilities and monetary values to potential losses. It provides a more precise assessment of risks and their potential impact.
- Qualitative Analysis: Relies on expert judgment, narratives, and subjective assessments to evaluate risks. Qualitative analysis is often used when precise data is unavailable or when assessing risks that are difficult to quantify.
The choice between quantitative and qualitative analysis should be based on the specific characteristics of the risks being assessed.
Risk Assessment Models and Methods
Various models and methods are available to facilitate risk analysis. Familiarize yourself with these tools to conduct a thorough evaluation:
- Decision Trees: Decision trees help you visualize decision-making processes and their associated risks, allowing you to identify optimal choices and potential pitfalls.
- Monte Carlo Simulation: This statistical technique models risk by simulating various scenarios and their probabilities, providing insights into potential outcomes.
- Sensitivity Analysis: Helps you understand how changes in specific variables or parameters can affect the overall risk profile.
- Risk Matrices: Risk matrices combine probability and impact assessments to categorize risks into high, medium, or low-risk categories, aiding in prioritization.
Select the most suitable model or method based on the complexity of the risk and the available data.
Probability and Impact Assessment
To analyze risks effectively, it’s essential to assess both their probability and potential impact:
- Probability Assessment: Determine the likelihood of each risk occurring, considering historical data, expert opinions, and available information. Probability is often expressed as a percentage.
- Impact Assessment: Evaluate the potential consequences of each risk, encompassing both the immediate and long-term effects on your project, organization, or objectives.
By combining probability and impact assessments, you can prioritize risks and allocate resources efficiently.
Data Collection and Analysis Tools
Effective data collection and analysis are at the heart of risk analysis. Employ various tools and techniques to gather and assess relevant data:
- SWOT Analysis: A structured approach to evaluate strengths, weaknesses, opportunities, and threats, helping identify internal and external factors that may impact your risk landscape.
- PESTEL Analysis: Analyzes political, economic, social, technological, environmental, and legal factors that can influence risks.
- Risk Heat Maps: Visual representations that display the level of risk associated with specific events or scenarios, allowing for a quick overview of risk profiles.
Utilize these tools to gain deeper insights into potential risks and their implications, facilitating informed decision-making during risk assessment.
Risk Evaluation
Risk evaluation is a critical phase within the risk assessment process. It involves assessing the significance of identified risks, understanding their potential impacts, and determining how your organization should respond to them. Let’s explore each component of risk evaluation in more detail:
Risk Severity Assessment
Risk severity assessment is the process of evaluating the potential consequences of each identified risk. To assess risk severity effectively:
- Consequence Analysis: Examine the full spectrum of potential consequences that a risk could have on your project, organization, or objectives. Consider both direct and indirect impacts.
- Scoring Systems: Develop a scoring system or scale that quantifies the severity of risks. For example, you could use a scale from 1 to 5, with 1 indicating minor consequences and 5 indicating catastrophic impacts.
- Stakeholder Involvement: Engage relevant stakeholders to provide insights into the potential severity of risks. Different perspectives can enhance the accuracy of severity assessments.
- Scenario Analysis: Create hypothetical scenarios for each risk, exploring various outcomes and their severity levels.
By thoroughly assessing risk severity, you can prioritize your risk management efforts, focusing on those risks with the highest potential for significant consequences.
Risk Prioritization
Risk prioritization involves ranking risks based on their severity, likelihood, and potential impact. Here’s how you can prioritize risks effectively:
- Risk Scoring Model: Develop a scoring model that combines the severity and likelihood of each risk to assign an overall risk score. This score helps rank risks in order of importance.
- Risk Matrix: Create a risk matrix that visually represents the relationship between likelihood and severity, categorizing risks into high, medium, or low priority.
- Risk Weighting: Assign weights to different risk factors, such as assigning higher importance to risks with the potential for severe consequences.
- Continuous Review: Regularly update risk prioritization as new information becomes available or as project circumstances change.
Prioritizing risks ensures that resources and attention are directed toward addressing the most critical threats and opportunities first.
Risk Tolerance and Acceptance
Determining your organization’s risk tolerance is a crucial step in risk evaluation. Consider the following factors when assessing risk tolerance:
- Defining Risk Tolerance: Clearly define the level of risk that your organization is willing to accept. This should align with your organization’s overall goals, industry standards, and strategic direction.
- Threshold Criteria: Establish specific criteria that determine when a risk can be accepted without further mitigation efforts. This may include risks with a low likelihood of occurrence or risks that are within predefined limits.
- Risk Appetite: Understand your organization’s appetite for risk, which reflects its willingness to take on risks to achieve its objectives. This appetite guides risk tolerance decisions.
Understanding and setting risk tolerance levels helps your organization make informed decisions about which risks to actively mitigate and which to accept.
Stakeholder Communication
Effective communication with stakeholders is crucial throughout the risk evaluation process. To ensure successful stakeholder communication:
- Identify Key Stakeholders: Identify all relevant stakeholders, including executives, project teams, investors, regulatory bodies, and affected parties.
- Clear Reporting: Develop a clear and concise reporting mechanism that communicates risk assessment findings, prioritization, and mitigation plans.
- Customized Messaging: Tailor your communication approach based on the audience’s level of expertise and interest in risk-related matters.
- Feedback Mechanisms: Establish channels for stakeholders to provide feedback, ask questions, and express concerns related to risk assessment.
Open and transparent communication fosters a collaborative environment and ensures that stakeholders are well-informed and engaged in the risk management process.
Risk Mitigation Strategies
Risk mitigation strategies are essential for reducing the impact of identified risks and improving the chances of successful outcomes. Let’s explore the key elements of risk mitigation strategies in more detail:
Risk Avoidance
Risk avoidance aims to eliminate risks by altering your project plans, strategies, or activities. Strategies for risk avoidance include:
- Plan Adjustments: Modify project scope, timelines, or objectives to eliminate high-impact risks.
- Process Reengineering: Redesign processes or workflows to eliminate potential bottlenecks or vulnerabilities.
- Resource Allocation: Allocate additional resources or expertise to mitigate potential resource constraints.
- Market Entry Adjustments: Change market entry strategies, target demographics, or product features based on market risk assessments.
Risk avoidance is a proactive approach that seeks to prevent risks from materializing altogether, often by altering your approach.
Risk Reduction
Risk reduction strategies focus on minimizing the likelihood or impact of identified risks. Methods for risk reduction include:
- Quality Control: Implement rigorous quality control measures to reduce the likelihood of defects or errors.
- Diversification: Spread investments or resources across multiple options to reduce exposure to a single risk.
- Security Measures: Enhance security protocols, both physical and digital, to protect against potential threats.
- Training and Skill Development: Invest in employee training and development to enhance skills and reduce the likelihood of human error.
Risk reduction aims to mitigate risks while allowing your organization to proceed with your project or objectives.
Risk Transfer
Risk transfer involves shifting the responsibility for specific risks to third parties or insurance providers. Risk transfer strategies include:
- Insurance Policies: Purchase insurance policies that cover specific risks, such as property insurance, liability insurance, or cyber insurance.
- Outsourcing: Transfer operational risks by outsourcing specific functions or processes to third-party service providers.
- Contractual Agreements: Use contractual agreements that allocate risks to the party best equipped to manage them effectively.
Risk transfer allows your organization to share the burden of certain risks, reducing the financial impact and potential liability.
Risk Acceptance
Risk acceptance involves acknowledging that some risks are within acceptable limits and do not require active mitigation. Key considerations for risk acceptance include:
- Defined Criteria: Establish clear criteria for when a risk can be accepted, such as risks with a low likelihood or risks with manageable consequences.
- Monitoring: Even when risks are accepted, continue to monitor them to detect changes in risk conditions or new information.
- Contingency Planning: Develop contingency plans outlining specific actions to take if a risk that has been accepted materializes.
Risk acceptance should be a conscious decision, aligned with your organization’s risk tolerance and strategic objectives.
Contingency Planning
Contingency planning involves developing strategies and actions to respond effectively if identified risks materialize. Consider these elements when creating contingency plans:
- Response Plans: Outline specific steps to take in response to different risk scenarios, including roles and responsibilities.
- Resource Allocation: Ensure that necessary resources, such as personnel, equipment, or funding, are readily available.
- Communication Protocols: Establish clear communication channels and procedures for alerting stakeholders and team members in the event of a risk occurrence.
- Testing and Drills: Regularly test contingency plans through simulations or drills to ensure readiness.
Effective contingency planning minimizes the impact of unforeseen events, allowing your organization to respond swiftly and recover efficiently from adverse situations.
How to Monitor and Review Risks?
Monitoring and reviewing risks is a continuous and essential aspect of effective risk management. It ensures that your organization stays vigilant and adaptable in the face of evolving circumstances. Let’s explore the key components of monitoring and reviewing risks in more detail:
Ongoing Risk Assessment
Ongoing risk assessment is the practice of regularly evaluating and reassessing identified risks to account for changes in the internal and external environment. Here’s how to effectively conduct ongoing risk assessment:
- Regular Updates: Continuously update your risk register and assessment as new information becomes available or as your project progresses.
- Periodic Reviews: Set a schedule for regular reviews, which may be monthly, quarterly, or annually, depending on the nature of the project and industry.
- Environmental Scanning: Keep a keen eye on external factors, such as market conditions, regulatory changes, and emerging trends, that may introduce new risks or alter existing ones.
- Stakeholder Input: Engage stakeholders in the ongoing risk assessment process to incorporate their insights and concerns.
Ongoing risk assessment ensures that your risk management strategies remain relevant and adaptive.
Key Performance Indicators (KPIs)
Key Performance Indicators (KPIs) are metrics that help you measure the effectiveness of your risk management efforts and identify trends or areas of concern. Consider the following when defining KPIs for risk monitoring:
- Relevance: Select KPIs that align with your organization’s objectives and the specific risks you’re managing.
- Measurability: Ensure that KPIs are quantifiable and can be tracked over time.
- Thresholds: Set clear thresholds or target values for each KPI, indicating acceptable and unacceptable performance levels.
- Regular Reporting: Establish a reporting schedule to track and communicate KPIs to relevant stakeholders.
KPIs provide a data-driven approach to monitoring risks and assessing the impact of risk management strategies.
Reporting and Documentation
Comprehensive reporting and documentation are essential for transparency, accountability, and informed decision-making. Here’s how to approach reporting and documentation in risk monitoring:
- Regular Reporting: Develop a reporting schedule that includes regular updates on the status of identified risks, their current impact, and the effectiveness of mitigation strategies.
- Clear Documentation: Maintain well-organized records of risk assessments, risk registers, mitigation plans, and any changes or updates made during ongoing risk assessment.
- Communication Channels: Define the channels and recipients for risk-related reporting. Ensure that reports are accessible to relevant stakeholders.
- Performance Trends: Use historical data and trends to analyze the effectiveness of risk management strategies and make necessary adjustments.
Effective reporting and documentation provide a solid foundation for strategic decision-making and demonstrate your organization’s commitment to risk management.
Continuous Improvement
Continuous improvement is the process of refining your risk management strategies based on lessons learned and evolving circumstances. Consider these aspects when focusing on continuous improvement:
- Lessons Learned: Regularly conduct post-incident reviews or post-project evaluations to identify areas for improvement.
- Feedback Loops: Encourage feedback from team members and stakeholders to gather insights on the effectiveness of risk mitigation efforts.
- Adaptation: Be prepared to adapt your risk management strategies in response to changing risk landscapes, emerging threats, or organizational shifts.
- Benchmarking: Compare your risk management practices with industry benchmarks and best practices to identify areas where improvements can be made.
Embracing a culture of continuous improvement ensures that your organization remains resilient and responsive in the face of evolving risks.
Risk Assessment Tools
Effective risk assessment relies on a variety of tools and methodologies to gather, analyze, and manage information about potential risks. These tools are essential for a structured and systematic approach to risk assessment. Here, we explore some of the key tools commonly used in the process:
1. Risk Assessment Matrix
A risk assessment matrix is a fundamental tool that visually represents the likelihood and severity of identified risks. Typically, it uses a grid format with likelihood on one axis and severity on the other. Risks are placed within the matrix based on their assessed likelihood and potential impact, helping to prioritize them. Commonly used categories for likelihood and severity include low, medium, and high, or numerical scales.
Benefits: Risk matrices provide a clear, at-a-glance view of risk prioritization, making it easier for decision-makers to focus on high-priority risks.
2. SWOT Analysis
SWOT (Strengths, Weaknesses, Opportunities, Threats) analysis is a strategic planning tool used to identify internal and external factors that can affect an organization’s objectives. In the context of risk assessment, the “T” (Threats) component focuses on identifying potential risks and vulnerabilities. SWOT analysis helps in understanding the broader context in which risks exist and assessing their impact on strategic planning.
Benefits: SWOT analysis provides a comprehensive view of the organization’s internal strengths and weaknesses alongside external threats and opportunities, offering a holistic perspective for risk assessment.
3. Risk Registers
A risk register is a systematic and organized document that records and tracks identified risks throughout the risk assessment process. It typically includes details such as risk descriptions, potential consequences, likelihood assessments, risk owners, and mitigation strategies. Risk registers serve as central repositories of risk-related information and enable continuous monitoring.
Benefits: Risk registers help maintain a structured record of risks, facilitating ongoing assessment, communication, and decision-making within an organization.
4. Quantitative Risk Analysis Tools
Quantitative risk analysis tools involve using numerical data and mathematical models to assess risks quantitatively. Common tools in this category include Monte Carlo simulations, decision trees, and probabilistic modeling. These tools provide more precise estimates of risk impact and likelihood and are especially valuable when dealing with complex projects or financial decisions.
Benefits: Quantitative risk analysis tools offer a higher level of precision in risk assessment, aiding in more accurate decision-making and resource allocation.
5. Risk Assessment Software
Risk assessment software tools are designed to streamline and automate various aspects of risk assessment processes. These tools often include features for risk identification, analysis, modeling, reporting, and collaboration. They can be customized to suit specific industries and organizational needs.
Benefits: Risk assessment software enhances efficiency by centralizing data, automating calculations, and enabling collaborative risk assessment among team members and stakeholders.
6. Brainstorming and Delphi Method
Qualitative risk assessment often begins with brainstorming sessions involving stakeholders and experts. The Delphi method, a structured and iterative approach, is employed to reach a consensus on potential risks and their characteristics. It involves multiple rounds of anonymous feedback and controlled communication.
Benefits: Brainstorming and the Delphi method harness collective intelligence, ensuring that a wide range of perspectives and risks are considered during the assessment.
7. Bowtie Risk Analysis
The bowtie risk analysis method is used to visualize and analyze the relationships between hazards, threats, controls, consequences, and risk events. It creates a graphical representation resembling a bowtie, which provides a clear overview of the risk scenario and the critical control measures in place.
Benefits: Bowtie analysis offers a visual and intuitive way to understand and communicate complex risk scenarios and the effectiveness of control measures.
These tools are not mutually exclusive and can be used in combination to tailor the risk assessment process to the specific needs and complexity of the situation. Selecting the right tools and methodologies is a crucial step in conducting effective risk assessments, ensuring that organizations can proactively manage and mitigate potential risks.
Risk Assessment Template
A risk assessment template is a pre-structured document or digital form designed to guide and standardize the risk assessment process. These templates are invaluable tools for organizations and individuals seeking to conduct thorough and consistent risk assessments across various scenarios. Below, we delve into the details of a risk assessment template, its components, and how to use it effectively:
Components of a Risk Assessment Template
- Title and Date: The template typically begins with a title that identifies the project, activity, or context under assessment. Include the date of the assessment to indicate its relevancy.
- Introduction: Provide a brief overview of the purpose of the risk assessment, its scope, and any relevant background information.
- Risk Identification: This section prompts users to list and describe potential risks associated with the project or activity. It may include fields for risk names, descriptions, and initial assessments.
- Risk Analysis: Here, users are guided to assess the identified risks more comprehensively. This includes evaluating the likelihood of each risk occurring and the potential impact it may have. Some templates use numerical scales or qualitative descriptors (e.g., low, medium, high) for these assessments.
- Risk Prioritization: Based on the analysis, this section helps prioritize risks by calculating a risk score or ranking. This allows users to focus on addressing the most critical risks first.
- Risk Mitigation: Users outline the strategies and actions planned to mitigate or manage each risk. This includes specifying responsible individuals, deadlines, and resources required for mitigation.
- Monitoring and Review: This part of the template addresses how the organization or individual will monitor and review risks over time. It includes details about the frequency of reviews and the criteria for triggering reviews or updates.
- Documentation and Reporting: Specify where and how risk assessment records will be stored, as well as reporting procedures and responsibilities for communicating risk assessment findings.
Using a Risk Assessment Template Effectively
To make the most of a risk assessment template, consider the following best practices:
- Customization: Tailor the template to the specific needs and context of your project or activity. Not all risks are relevant in every situation, so adapt the template accordingly.
- Involvement: Engage relevant stakeholders, experts, and team members in the risk assessment process. Their insights and expertise can enhance the accuracy and comprehensiveness of the assessment.
- Consistency: Use the template consistently across different projects or activities to ensure that risk assessments are comparable and provide valuable insights for decision-making.
- Regular Updates: Risk assessments should not be static documents. Regularly revisit and update the assessment as circumstances change or new information becomes available.
- Communication: Share the results of the risk assessment with all relevant parties, including team members, stakeholders, and decision-makers. Clear communication is essential for aligning efforts and ensuring everyone is aware of potential risks.
- Training: If your organization regularly conducts risk assessments, consider providing training on using the template effectively to ensure a common understanding of the process.
Benefits of Using a Risk Assessment Template
Utilizing a risk assessment template offers several advantages:
- Consistency: Templates provide a standardized framework for risk assessment, ensuring that key elements are consistently addressed.
- Efficiency: They streamline the risk assessment process, saving time and effort compared to creating assessments from scratch.
- Comprehensive Coverage: Templates prompt users to consider various aspects of risk, from identification to mitigation, enhancing the depth and breadth of assessments.
- Transparency: Templates document the risk assessment process, making it transparent and accessible to all relevant parties.
- Historical Record: Templates serve as a historical record of risk assessments, enabling organizations to track changes over time and learn from past assessments.
Incorporating a risk assessment template into your risk management practices can significantly enhance your ability to identify, analyze, and mitigate potential risks effectively. Whether you are managing a project, evaluating a business venture, or assessing risks in other contexts, a well-designed template is a valuable tool for informed decision-making and risk management.
Risk Assessment Examples
Understanding risk assessment examples provides valuable insights into the practical application of risk assessment principles across various industries and scenarios. Here, we delve into several detailed examples that illustrate how risk assessment plays a pivotal role in decision-making and risk management:
1. Financial Services
Risk Type: Credit Risk, Market Risk, Operational Risk
Example Scenario: A commercial bank is considering lending a substantial amount of capital to a medium-sized business. Before extending the loan, the bank conducts a comprehensive risk assessment:
Key Risk Assessment Activities:
- Credit Risk Assessment: The bank evaluates the borrower’s creditworthiness by analyzing their financial statements, credit history, and industry outlook. Credit scores, financial ratios, and historical default rates are used to quantify credit risk.
- Market Risk Assessment: In the context of this loan, market risk arises from economic fluctuations that could affect the borrower’s ability to repay. The bank assesses market conditions, interest rate movements, and currency exchange rates to gauge potential market risks.
- Operational Risk Assessment: The bank identifies potential operational risks, such as errors in loan processing, data breaches, or internal fraud. Risk assessments in this area may involve process mapping and vulnerability analysis.
Mitigation Strategies: Based on the risk assessment, the bank may decide to approve the loan with specific conditions, require collateral, or adjust the interest rate to compensate for higher risks. Continuous monitoring of the borrower’s financial health and market conditions is also crucial to mitigate risks effectively.
2. Healthcare
Risk Type: Patient Safety Risks
Example Scenario: A large hospital aims to enhance patient safety by conducting a risk assessment:
Key Risk Assessment Activities:
- Medication Safety Assessment: The hospital assesses the risk of medication errors by analyzing medication administration processes, staff training, and error reporting systems. Data on near-misses and adverse events are examined.
- Infection Control Assessment: Infection risks are evaluated through surveillance of healthcare-associated infections, hand hygiene compliance, and adherence to sterilization protocols.
- Equipment Safety Assessment: Risks related to medical equipment malfunction or misuse are assessed. This may involve preventive maintenance checks, training for equipment users, and audits of equipment safety features.
Mitigation Strategies: The hospital implements a range of strategies to mitigate identified risks, including staff training, process improvements, the introduction of safety protocols, and regular equipment maintenance. Continuous monitoring and feedback mechanisms are established to ensure ongoing patient safety.
3. Manufacturing
Risk Type: Supply Chain Risks, Quality Control Risks, Workplace Safety Risks
Example Scenario: A manufacturing company that produces automotive parts conducts a risk assessment to ensure operational continuity:
Key Risk Assessment Activities:
- Supply Chain Risk Assessment: The company evaluates potential disruptions in its supply chain, such as delays in raw material deliveries, transportation issues, and geopolitical risks. A risk matrix may be used to prioritize supply chain vulnerabilities.
- Quality Control Assessment: To maintain product quality, the company assesses risks related to defects, manufacturing errors, and product recalls. Statistical process control (SPC) charts and failure mode and effects analysis (FMEA) are employed.
- Workplace Safety Assessment: Risks associated with workplace accidents and injuries are examined. The assessment includes hazard identification, safety training evaluation, and incident reporting analysis.
Mitigation Strategies: Mitigation strategies may include dual sourcing of critical components, implementing quality control processes, and enhancing workplace safety protocols. Regular audits and inspections help ensure ongoing risk mitigation.
4. Technology
Risk Type: Cybersecurity Risks
Example Scenario: A technology company that manages sensitive customer data conducts a cybersecurity risk assessment:
Key Risk Assessment Activities:
- Threat Assessment: The company identifies potential cybersecurity threats, such as phishing attacks, malware, and data breaches. It assesses the frequency and severity of these threats.
- Vulnerability Assessment: The company evaluates its own vulnerabilities, including weaknesses in network security, software vulnerabilities, and employee security awareness.
- Impact Assessment: The assessment considers the potential impact of a cybersecurity incident, including financial losses, damage to reputation, and regulatory penalties.
Mitigation Strategies: Mitigation strategies involve implementing robust cybersecurity measures, such as firewalls, intrusion detection systems, encryption, and employee training on cybersecurity best practices. Regular penetration testing and incident response planning are part of the risk mitigation plan.
5. Environmental
Risk Type: Environmental Risks
Example Scenario: A renewable energy company plans to build a wind farm in a coastal area. Before proceeding, the company conducts an environmental risk assessment:
Key Risk Assessment Activities:
- Ecological Impact Assessment: The company assesses potential impacts on local ecosystems, including bird migration patterns, marine life habitats, and vegetation. Expert ecologists may be involved.
- Regulatory Compliance Assessment: Regulatory risks related to environmental laws and permits are evaluated. The assessment ensures compliance with environmental impact assessment (EIA) requirements.
- Climate Change Risk Assessment: The company considers long-term climate change risks, such as sea level rise and extreme weather events, to assess their impact on the wind farm’s operation and infrastructure.
Mitigation Strategies: Mitigation strategies may include habitat restoration, adherence to environmental regulations, and the development of a comprehensive environmental management plan. The company may also commit to ongoing monitoring and adaptive management to address changing environmental conditions.
These examples highlight the diverse applications of risk assessment across industries. By studying these cases, you can gain insights into tailoring risk assessment methodologies to specific contexts and mitigating risks effectively.
Conclusion
Risk assessment is a powerful tool that helps individuals and organizations make informed decisions and navigate the complexities of the world. By identifying, analyzing, and mitigating risks, you can safeguard your projects, investments, and objectives. Remember, risk assessment is not a one-time task; it’s an ongoing process that requires vigilance and adaptability. So, embrace the principles outlined in this guide, tailor them to your specific needs, and always strive for continuous improvement.
As you embark on your risk assessment journey, keep in mind that examples from various industries provide valuable insights into the practical application of risk assessment principles. Whether you’re in finance, healthcare, manufacturing, technology, or environmental fields, the fundamental principles of risk assessment remain consistent. By learning from these examples and applying the strategies outlined in this guide, you can confidently face uncertainty and make more informed decisions, ultimately enhancing your ability to achieve success and manage risks effectively.
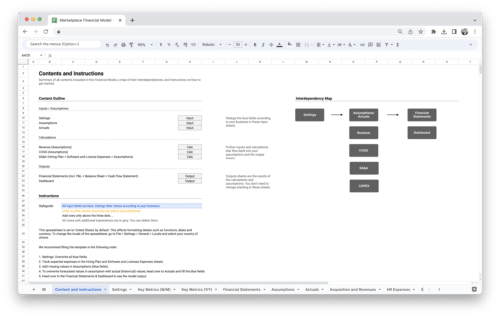
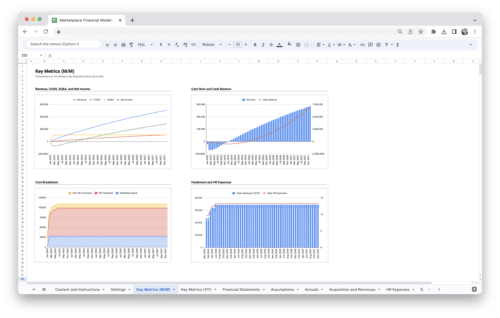
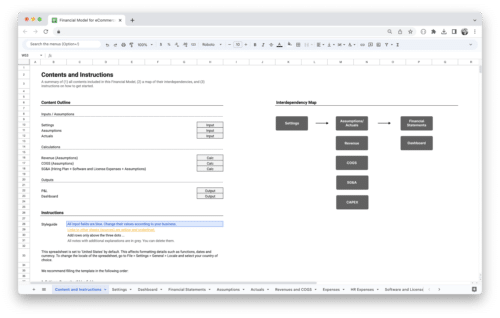
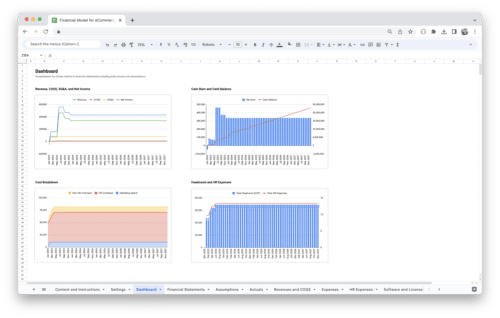
Get Started With a Prebuilt Template!
Looking to streamline your business financial modeling process with a prebuilt customizable template? Say goodbye to the hassle of building a financial model from scratch and get started right away with one of our premium templates.
- Save time with no need to create a financial model from scratch.
- Reduce errors with prebuilt formulas and calculations.
- Customize to your needs by adding/deleting sections and adjusting formulas.
- Automatically calculate key metrics for valuable insights.
- Make informed decisions about your strategy and goals with a clear picture of your business performance and financial health.